A research de-identification checklist form ensures sensitive information is systematically removed to protect participant privacy. This tool guides researchers through essential steps like anonymizing data points, verifying consent, and documenting data handling procedures. Following such a checklist minimizes risks and enhances compliance with ethical standards and legal regulations.
Research De-Identification Checklist Form Sample PDF Viewer
Image example of Research De-Identification Checklist Form:
Research De-Identification Checklist Form Samples
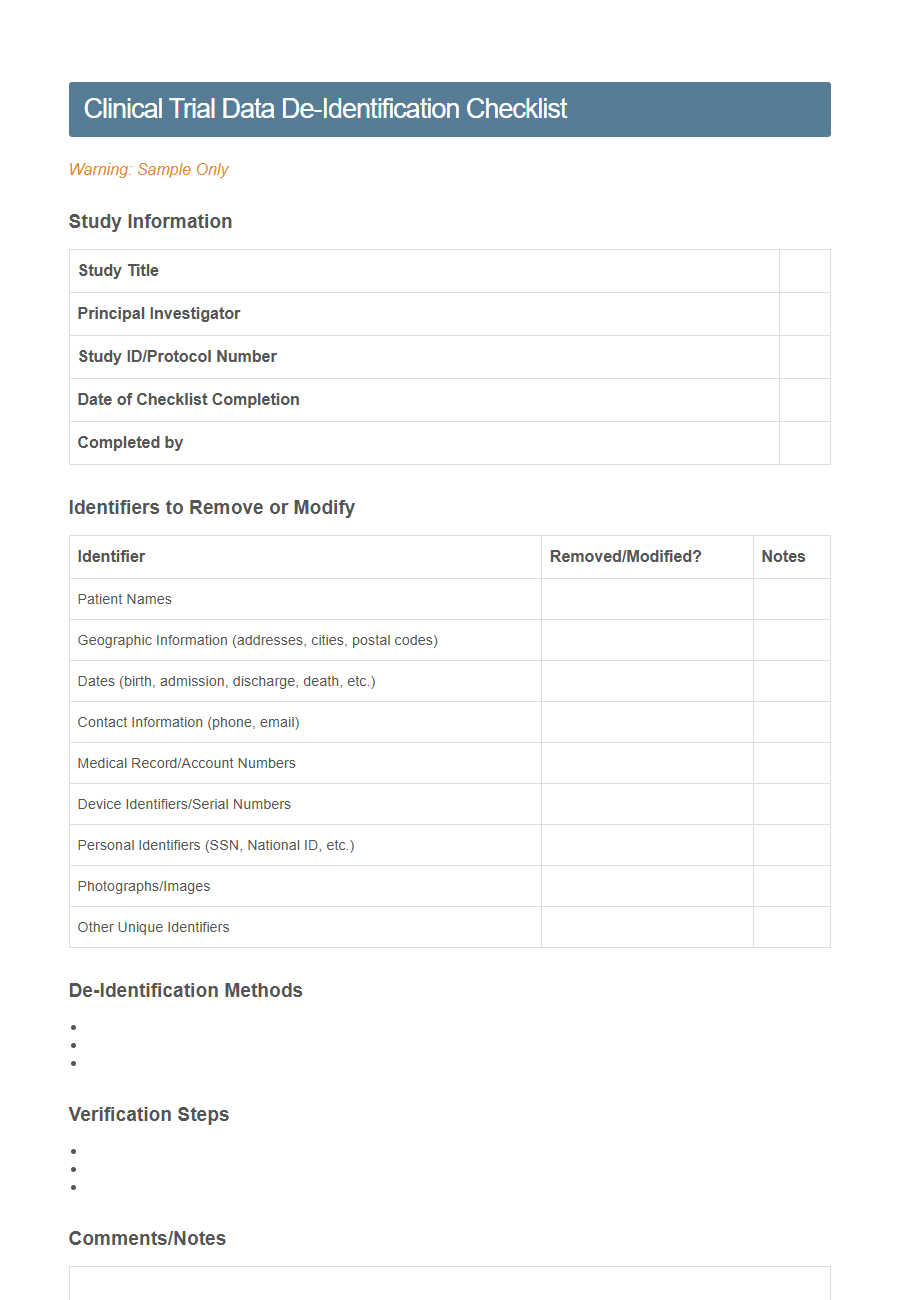
Clinical Trial Data De-Identification Checklist - PDF - HTML
Patient Interview Transcript De-Identification Form - PDF - HTML
Focus Group Record De-Identification Checklist - PDF - HTML
Genetic Research Data De-Identification Template - PDF - HTML
Survey Response De-Identification Checklist - PDF - HTML
Case Study Report De-Identification Form - PDF - HTML
Audio Recording De-Identification Checklist - PDF - HTML
Video Data De-Identification Template - PDF - HTML
Medical Image De-Identification Checklist - PDF - HTML
Social Media Research De-Identification Form - PDF - HTML
Educational Data De-Identification Checklist - PDF - HTML
Laboratory Results De-Identification Form - PDF - HTML
Mental Health Records De-Identification Checklist - PDF - HTML
Pharmacovigilance Data De-Identification Template - PDF - HTML
Mobile Health App Data De-Identification Checklist - PDF - HTML
Introduction to Research De-Identification
Research de-identification is a critical process to protect participant privacy while enabling data use. Proper de-identification ensures compliance with regulatory standards and ethical guidelines.
- Purpose of De-Identification - It involves removing or masking personal identifiers to prevent the re-identification of individuals.
- Regulatory Compliance - De-identification aligns research practices with legal requirements such as HIPAA and GDPR to safeguard sensitive information.
- Data Utility Balance - Effective de-identification maintains data usefulness for research while minimizing privacy risks.
Importance of De-Identification in Research
De-identification in research is critical for protecting participant privacy and ensuring ethical standards. It minimizes the risk of personal data exposure while enabling valuable data analysis.
- Protects participant confidentiality - Removing identifiers prevents unauthorized access to sensitive information.
- Ensures compliance with regulations - Adhering to privacy laws like HIPAA maintains legal and ethical research standards.
- Facilitates data sharing - De-identified data can be shared more freely, promoting collaboration and advancing scientific knowledge.
Using a Research De-Identification Checklist Form helps systematically verify that all necessary steps are taken to safeguard participant information.
Key Principles of Data De-Identification
The Research De-Identification Checklist Form ensures that personal data is anonymized to protect participant privacy.
Key principles of data de-identification include removing direct identifiers and minimizing the risk of re-identification through indirect identifiers. These principles help maintain data utility while safeguarding sensitive information in research projects.
Essential Elements of a De-Identification Checklist Form
What are the essential elements of a Research De-Identification Checklist Form? The form must include identifiers that are removed or masked to protect participant privacy. It should also document the methods used to achieve de-identification and ensure compliance with relevant regulations.
Why is it important to specify the types of data being de-identified? Identifying whether the data includes direct or indirect identifiers helps tailor the de-identification process appropriately. This prevents re-identification risks and maintains data integrity for research use.
How does the checklist address data handling procedures? It outlines protocols for data access, storage, and sharing to safeguard confidentiality. Clear guidelines reduce the chance of unauthorized disclosures throughout the research lifecycle.
What role does the checklist play in regulatory compliance? It ensures that the de-identification process aligns with legal standards such as HIPAA or GDPR. Proper documentation supports audit readiness and ethical research practices.
Why must the checklist include a verification step for de-identification? Verification confirms that the data is properly anonymized and risk of re-identification is minimized. This step is critical to maintaining trust with research participants and stakeholders.
Identifying and Classifying Personal Identifiers
The Research De-Identification Checklist Form is essential for identifying and classifying personal identifiers to ensure data privacy. It helps researchers systematically recognize direct and indirect identifiers that could reveal individual identities. Proper classification aids in applying appropriate de-identification techniques to protect participant confidentiality.
Step-by-Step De-Identification Procedures
The Research De-Identification Checklist Form provides a structured approach to ensure the removal of all personally identifiable information from research data. This process safeguards participant privacy while maintaining the integrity of the dataset for analysis.
Step-by-step de-identification procedures guide researchers through each necessary action to effectively anonymize data.
Documentation and Record-Keeping Requirements
The Research De-Identification Checklist Form ensures that all steps taken to remove identifying information are thoroughly documented. Accurate record-keeping provides a clear audit trail for compliance and verification purposes. Maintaining detailed documentation supports transparency and accountability throughout the research process.
Compliance with Legal and Ethical Standards
The Research De-Identification Checklist Form ensures compliance with legal and ethical standards by systematically verifying the removal of personally identifiable information from research data.
This process protects participant privacy and aligns with regulations such as HIPAA and GDPR. Researchers use the checklist to confirm adherence to institutional review board (IRB) guidelines and maintain data confidentiality throughout the study.
Quality Assurance and Risk Mitigation Strategies
Ensuring the accuracy and completeness of data de-identification processes is critical for maintaining research integrity. Implementing robust risk mitigation strategies protects participant privacy and complies with regulatory standards.
- Quality Control Procedures - Establish systematic checks to verify data removal and anonymization accuracy throughout the de-identification process.
- Risk Assessment Protocols - Identify and evaluate potential vulnerabilities that could lead to re-identification risks or data breaches.
- Documentation and Review - Maintain detailed records of de-identification steps and conduct periodic audits to ensure ongoing compliance and effectiveness.
